| Risque cyber
Les Passkeys : la solution qui réconcilie simplicité et sécurité ?
Les passkeys sont une alternative pratique et sûre à l’authentification par mot de passe. Pour mieux comprendre les passkeys, découvrez quelles sont leurs utilités, comment elles fonctionnent et comment ces clés d’accès peuvent changer la manière dont vous protégez vos données personnelles en ligne !
Comment ça marche ? Quels avantages face aux mots de passe ?
Les passkeys sont un dispositif de remplacement des mots de passe développé par l’alliance FIDO (Alliance Fast Identity Online), un regroupement d’entreprises souhaitant réduire la dépendance aux mots de passe dans le monde numérique. En effet, il est de notoriété publique que les mots de passe posent d’importants problèmes de sécurité, et ne sont pas totalement fiables. Encore en 2022, 89 % des entreprises rapportaient avoir été victimes de campagnes de phishing (vols de mot de passe).
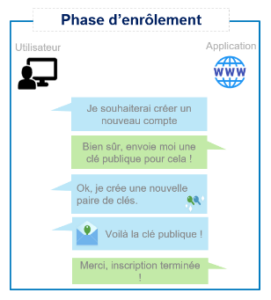
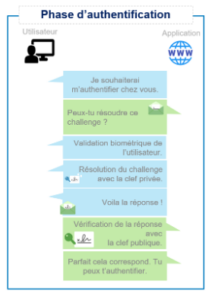
A chaque connexion, l’application demandera à l’utilisateur de résoudre un challenge dont la réponse ne peut être produite qu’à partir d’une clef privée. Évidemment, toutes ces actions sont transparentes pour l’utilisateur, le seul prérequis étant la possession de la clef privée au moment de la connexion. Ce dernier n’aura qu’à renseigner son login puis autoriser l’authentification via une validation biométrique (FaceID, empreinte digitale, etc.) ou encore un code PIN.
Une expérience utilisateur améliorée
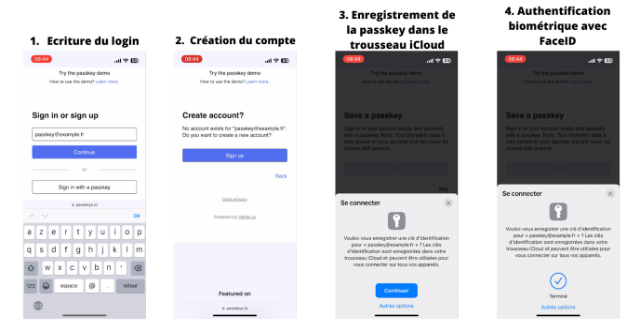
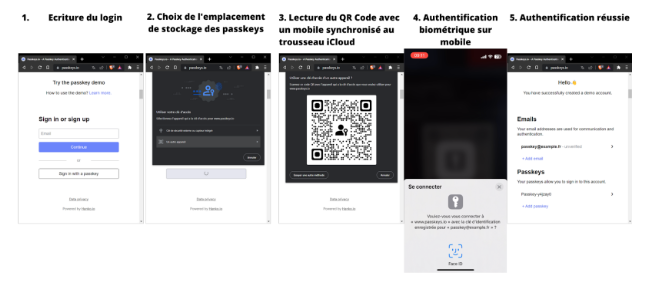
Voyons comment se traduisent les passkeys en termes d’expérience utilisateur. Ci-dessous, un exemple de la création d’un compte sur passkeys.io avec un téléphone :
L’adoption des passkeys et ses limites
De par leur construction, les passkeys ne sont pas liées à un seul appareil. Par exemple, les clefs privées peuvent être stockées sur iCloud et synchronisées entre plusieurs périphériques. Cela pose donc un véritable problème de sécurité pour les entreprises. En effet, les utilisateurs pourraient y accéder sur des appareils non managés par les politiques de sécurité de leur entreprise. Un périphérique non managé pourrait ainsi être synchronisé avec les passkeys professionnels de l’utilisateur, tout en étant vulnérable par manque de correctifs de sécurité. Une entreprise souhaitant déployer l’authentification par passkeys pour l’ensemble de ses terminaux (endpoints) doit absolument penser ce type de problèmes pour éviter des failles de sécurité potentielles.
L’alliance FIDO a encore de nombreux écueils, devant elle, pour démocratiser cette technologie mais l’avenir sera très certainement passwordless. Les passkeys sont un moyen de connexion sécurisé, user-friendly et dématérialisé n’offrant que des avantages comparées aux méthodes traditionnelles. Il ne fait aucun doute que cette technologie sera adoptée sur le long terme.
Thomas Halouis
Consultant Access Management


![Lire la suite à propos de l’article [Contribution] EFF.org : Multiples faiblesses de sécurité](https://m9z4y4q5.rocketcdn.me/wp-content/uploads/2018/03/eft-logo-1-300x193.png)



